
Executive Summary
Recently, threat actor(s) have been actively observed abusing public cloud service providers Amazon Web Services (AWS) and Microsoft Azure to host and deliver variants of three Remote Access Trojans (RATs) previously observed in malicious campaigns. A Cisco Talos report published on Wednesday, January 12, 2022 notes that victims of the campaign are being observed as residing primarily across the United States, Canada, Italy, and Singapore.
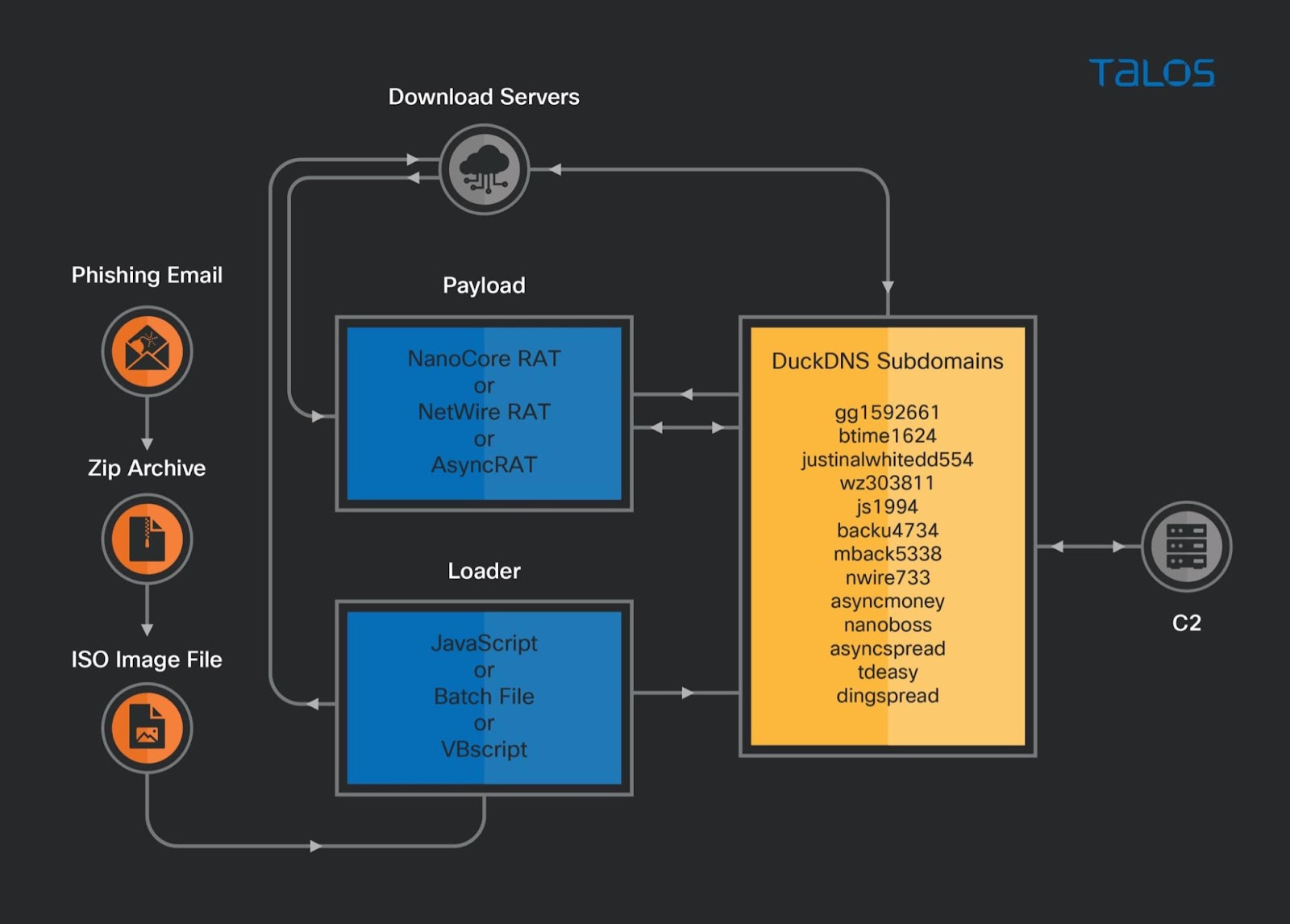
The malware has been identified as variants of AsyncRAT, NanoCore, and NetWire families and could allow a threat actor(s) to overtake control over a victims environment, leak information, and execute arbitrary code. Observations around the RAT deployment via public cloud infrastructure was first observed around October 26, 2021. The RAT payloads are utilizing free dynamic DNS service, DuckDNS. This allows a threat actor(s) to regularly change IP addresses of Command and Control (C2) servers and promptly add new subdomains.
Analysis
According to Cisco Talos, the trio of RAT variant families AsyncRAT, NanoCore, and NetWire were initially observed around October 26, 2021, with victims of the campaign being primarily located in the United States, Canada, Italy, and Singapore. The malicious campaign variants include several features that could allow a threat actor(s) to overtake control over a victims environment, leak information, and execute arbitrary code.
The initial infection is spread via a malicious phishing email that includes a ZIP attachment. The ZIP archive files contain a .ISO image with a malicious loader in the form of JavaScript, a Windows batch file (.bat), or Visual Basic script (VBScript). If the script is executed on the victims machine, it connects to a download server hosted on an AWS EC2 instance or Azure cloud based Windows server. The RAT payloads are utilizing free dynamic DNS service, DuckDNS. This allows the threat actor(s) to regularly change IP addresses of C2 servers and promptly add new subdomains.
AsyncRAT - A remote access tool utilized to remotely monitor and control computers through a secure encrypted connection. Threat actor(s) in this campaign could essentially adjust client setting configurations to connect to the C2 server, allowing access to the victim's machine.
NanocoreRAT - A 32-bit .NET portable executable first observed in 2013. After 2017, leaked versions of Nanocore were widely used by threat actors in campaigns.
NetwireRAT - Used by the threat actors to steal victim's login credentials/passwords and personally identifiable information (PII). NetwireRAT has the capability to perform remote code execute (RCE) and collect filesystem information.
Recommendations
- Organizations should monitor outgoing connections to cloud computing services for malicious traffic
- Reference Indicators of Compromise (IOCs) below for suspicious network traffic communications
- Implement rules around script execution policies
- Utilize email filtering and improve email security to detect and mitigate malicious email messages
References
1. C, Raghuprasad & V, Svajcer. "Nanocore, Netwire and AsyncRAT spreading campaign uses public cloud infrastructure", January 12, 2022. URL: https://blog.talosintelligence.com/2022/01/nanocore-netwire-and-asyncrat-spreading.html
2. R, Lakshmanan. "Hackers Use Cloud Services to Distribute Nanocore, Netwire, and AsyncRAT Malware", January 12, 2022. URL: https://thehackernews.com/2022/01/hackers-use-cloud-services-to.html
3. S, Nichols. "New RAT campaign abusing AWS, Azure cloud services", January 12, 2022. URL: https://www.techtarget.com/searchsecurity/news/252511913/New-RAT-campaign-abusing-AWS-Azure-cloud-services
4. B, Vigliarolo. "Cisco Talos discovers a new malware campaign using the public cloud to hide its tracks", January 12, 2022. URL: https://www.techrepublic.com/article/cisco-talos-discovers-a-new-malware-campaign-using-the-public-cloud-to-hide-its-tracks/
Indicators of Compromise (IOCs)
The following are IOCs provided by Cisco Talos.
13[.]82[.]65[.]56
103[.]151[.]123[.]194
194[.]156[.]90[.]26
52[.]27[.]15[.]250
23[.]102[.]1[.]5
137[.]135[.]65[.]29
40[.]85[.]140[.]7
52[.]150[.]26[.]35
btime1624[.]duckdns[.]org
justinalwhitedd554[.]duckdns[.]org
wz303811[.]duckdns[.]org
js1994[.]duckdns[.]org
backu4734[.]duckdns[.]org
www[.]backu4734[.]duckdns[.]org
mback5338[.]duckdns[.]org
nwire733[.]duckdns[.]org
asyncmoney[.]duckdns[.]org
nanoboss[.]duckdns[.]org
tdeasy[.]duckdns[.]org
dingspread[.]duckdns[.]org
asyncspread[.]duckdns[.]org
jw9428875[.]duckdns[.]org
meunknown[.]duckdns[.]org
asyncpcc[.]duckdns[.]org
yuri101[.]duckdns[.]org
hxxp://13.78.209[.]105/b/
hxxp://13.78.209[.]105/b/7632JUST.exe
hxxp://13.78.209[.]105/b/7632just.exe/
hxxp://13.78.209[.]105/b/8903mback.exe
hxxp://13.78.209[.]105/B/8903MBACK.exe
hxxp://13.78.209[.]105/B/AsyncClient7842.exe
hxxp://13.78.209[.]105/B/Host.exe
hxxp://13.78.209[.]105/D/Servers/
hxxp://13.78.209[.]105/D/Servers/7632JUST.js
hxxp://13.78.209[.]105/d/servers/8093mm.exe
hxxp://13.78.209[.]105/D/Servers/AsyncClient.exe
hxxp://13.78.209[.]105/d/servers/hostkfkk.exe
hxxp://13.78.209[.]105/D/Servers/Netwire_prevent.exe
hxxp://13.78.209[.]105/d/servers/netwire_prevent.exe
hxxp://13.78.209[.]105/E
hxxp://13.78.209[.]105/E/AsyncClient6121.exe
hxxp://13.78.209[.]105/E/ClientDC.exe
hxxp://13.78.209[.]105/E/Er.txt
hxxp://13.78.209[.]105/E/nano6129.exe
hxxp://13.78.209[.]105/E/New%20folder/7632.exe
hxxp://13.78.209[.]105/E/New%20folder/8903.exe
hxxp://13.78.209[.]105/E/New%20folder/Async7842.exe
hxxp://13.78.209[.]105/E/New%20folder/Host.exe
hxxp://btime1624.duckdns[.]org:7923/
hxxp://btime1624.duckdns[.]org:7923/Vre
hxxp://btime1624.duckdns[.]org/
hxxp://btime1624.duckdns[.]org/B
hxxp://btime1624.duckdns[.]org/b/7632just.exe
hxxp://btime1624.duckdns[.]org/B/7632JUST.exe/
hxxp://btime1624.duckdns[.]org/b/8903mback.exe
hxxp://btime1624.duckdns[.]org/B/8903MBACK.exe/
hxxp://btime1624.duckdns[.]org/B/Host.exe
hxxp://btime1624.duckdns[.]org/D/Servers/
hxxp://btime1624.duckdns[.]org/D/Servers/7632KL.exe
hxxp://btime1624.duckdns[.]org/d/servers/8093mm.exe
hxxp://btime1624.duckdns[.]org/d/servers/asyncclient.exe
hxxp://btime1624.duckdns[.]org/d/servers/hostkfkk.exe
hxxp://btime1624.duckdns[.]org/D/Servers/HostKfkk.exe
hxxp://btime1624.duckdns[.]org/D/Servers/Netwire_prevent.exe
hxxp://btime1624.duckdns[.]org/e/asyncclient6121.exe
hxxp://btime1624.duckdns[.]org/E/ClientDC.exe
hxxp://btime1624.duckdns[.]org/E/New%20folder/7632.exe
hxxp://btime1624.duckdns[.]org/E/New%20folder/8903.exe
hxxp://btime1624.duckdns[.]org/e/new%20folder/async7842.exe
hxxp://btime1624.duckdns[.]org/E/New%20folder/Async7842.exe
hxxp://btime1624.duckdns[.]org/E/New%20folder/Host.exe
hxxp://gg1592661.duckdns[.]org/
hxxp://gg1592661.duckdns[.]org/B/
hxxp://gg1592661.duckdns[.]org/b/
hxxp://gg1592661.duckdns[.]org/B/7632JUST.exe
hxxp://gg1592661.duckdns[.]org/b/7632just.exe
hxxp://gg1592661.duckdns[.]org/B/8903MBACK.exe
hxxp://gg1592661.duckdns[.]org/b/8903mback.exe
hxxp://gg1592661.duckdns[.]org/B/AsyncClient7842.exe
hxxp://gg1592661.duckdns[.]org/b/asyncclient7842.exe
hxxp://gg1592661.duckdns[.]org/b/Host.exe
hxxp://gg1592661.duckdns[.]org/b/host.exe
hxxp://gg1592661.duckdns[.]org/D/Servers/
hxxp://gg1592661.duckdns[.]org/d/servers/7632kl.exe
hxxp://gg1592661.duckdns[.]org/D/Servers/8093mm.exe
hxxp://gg1592661.duckdns[.]org/D/Servers/AsyncClient.exe
hxxp://gg1592661.duckdns[.]org/D/Servers/HostKfkk.exe
hxxp://gg1592661.duckdns[.]org/D/Servers/Netwire_prevent.exe
hxxp://gg1592661.duckdns[.]org/d/servers/netwire_prevent.exe
hxxp://gg1592661.duckdns[.]org/E
hxxp://gg1592661.duckdns[.]org/E/ClientDC.exe
hxxp://gg1592661.duckdns[.]org/E/nano6129.exe
hxxp://gg1592661.duckdns[.]org/E/New%20folder/7632.exe
hxxp://gg1592661.duckdns[.]org/E/New%20folder/8903.exe
hxxp://gg1592661.duckdns[.]org/E/New%20folder/Async7842.exe
hxxp://gg1592661.duckdns[.]org/e/new%20folder/async7842.exe
hxxp://gg1592661.duckdns[.]org/Vre
hxxps://btime1624.duckdns[.]org/
hxxps://btime1624.duckdns[.]org/B/Host.exe/
hxxps://gg1592661.duckdns[.]org/
hxxps://gg1592661.duckdns[.]org/B/AsyncClient7842.exe
hxxps://gg1592661.duckdns[.]org/C
hxxps://gg1592661.duckdns[.]org/D/Servers/
hxxps://gg1592661.duckdns[.]org/E/AsyncClient6121.exe
hxxp://194.156.90[.]26:8012/Vre
hxxp://52.27.15[.]250/A/behdhdjdj.txt
hxxp://52.27.15[.]250/A/SJJS.txt
hxxp://52.27.15[.]250/A/HSHSJSJD.txt
hxxp://nanoboss.duckdns[.]org/
hxxp://nanoboss.duckdns[.]org/
hxxp://23.102.1[.]5/
hxxp://asyncspread.duckdns[.]org/
hxxp://tdeasy.duckdns[.]org/Vre
tcp://asyncspread.duckdns[.]org:6121/
tcp://nanoboss.duckdns[.]org:6129/
hxxp://23.102.1[.]5:6129/
hxxp://tdeasy.duckdns[.]org/
hxxps://tdeasy.duckdns[.]org/
hxxp://tdeasy.duckdns[.]org:6128/
hxxp://tdeasy.duckdns[.]org:6128/Vre
hxxp://dingspread.duckdns[.]org/vre/*
hxxp://dingspread.duckdns[.]org:6130/
hxxp://dingspread.duckdns[.]org:6130/Vre
hxxp://jw9428875.duckdns[.]org:1991/Vre
hxxp://meunknown.duckdns[.]org/
hxxp://52.150.26[.]35/bypass.txt
hxxp://52.150.26[.]35/PE.txt
hxxp://52.150.26[.]35/pe.txt
hxxp://40.85.140[.]7/bypass.txt
hxxp://40.85.140[.]7/PE.txt
hxxp://40.85.140[.]7/pe.txt
hxxp://137.135.65[.]29/bypass.txt
hxxp://137.135.65[.]29/PE.txt
hxxp://137.135.65[.]29/pe.txt
44f5442b45a48365cdd6c7d1f16ba19dea4fb1865ea4e9178c5758929f59d0f7
e3f46470aa9ef52628f741e07db33a6af854693ae2a761d397bf87fbfbe687c9
5518f5e20b27a4b10ebc7abce37c733ab532354b5db6aed7edf19c25caba2ff3
8ffde50491ef1cfc93f417b731186a08fb6c3e5aad21f131a60b87936bd3f850
a5d5de41b6546981f2284c07aa2fe17ac0b15727fb96fdff33db020a0826810e
bbceba6fd06b01bd5c69ccab1ea106189455e1e85e577e278f9f362940b5442c
959484bfe98d39321a877e976a7cde13c9e2d0667a155dda17aeade58b68391c
7257729274b6ab5c1a605900fa40b2a76f386b3dbb3c0f4ab29e85b780eaef73
eae81605341641ad10c18ab60b79339617f0219abaa1ab5ee7883fc9d429b885
d42e5f2e60b39e2aca3dd09a4dd5803a04b33821e6da8808ef9ef450d6771e30
574b348f67921ce34f660afe2ff75d0538bd5ea203739a77479dba7f026f0476
6b4401690cb0a07ee98ff3c5fc351b20c6e0a4ba7474c6ad858e5dc69a60b36f
843c5f7a818681e3df212c80515cdce0bd56c6e178412736b8a22b15ebb35435
ff66be4a8df7bd09427a53d2983e693489fbe494edd0244053b29b9f048df136
988c1b9c99f74739edaf4e80ecaba04407e0ca7284f3dbd13c87a506bf0e97b7
4b61697d61a8835a503f2ea6c202b338bde721644dc3ec3e41131d910c657545
dfdb008304c3c2a5ec1528fe113e26088b6118c27e27e5d456ff39d300076451
c8c69f36f89061f4ce86b108c0ff12ade49d665eace2d60ba179a2341bd54c40
28ef1f6f0d8350a3fda0f604089288233d169946fca868c074fc16541b140055
b7f3d1dd2aa804eb498480b7a3b03ea003efb665005e844e51be5b8ab9dc8e79
68106918876232b746129b1161c3ac81914672776522f722062945f55166ba68
1dd6d37553168fa3929f5eaa5b2b0505aae5897809b532dd0b12eae8ffd8957f
1490f6303a675ded86c22841f87868c6f0867e922671e0426f499e46a72060d2
98e3e47c326aeb2e6001efca84737ae0ef78ce3576912aebfcbe05105db3f72a
c8dec500839b3698755d9304442aa9f3516218b7c6340e2b1202dbe83089ab1d